
Android users are being warned about a new strain of malware called Mazar Bot that is hitting smartphones, giving attackers full administrative rights to monitor and control nearly every aspect of the phone.
The manipulative and persistent piece of malware, found to be in active use by researchers at Heimdal Security, takes hold via a malware-ridden SMS/MMS message that, once clicked, spreads a torrent of alarming exploits such as sending malicious text messages, anonymously accessing the web, putting the phone into sleep mode and even fully erasing all content from the device.
Read more: Google Android: Smartphones hit with Mazar Bot malware that can 'erase everything'
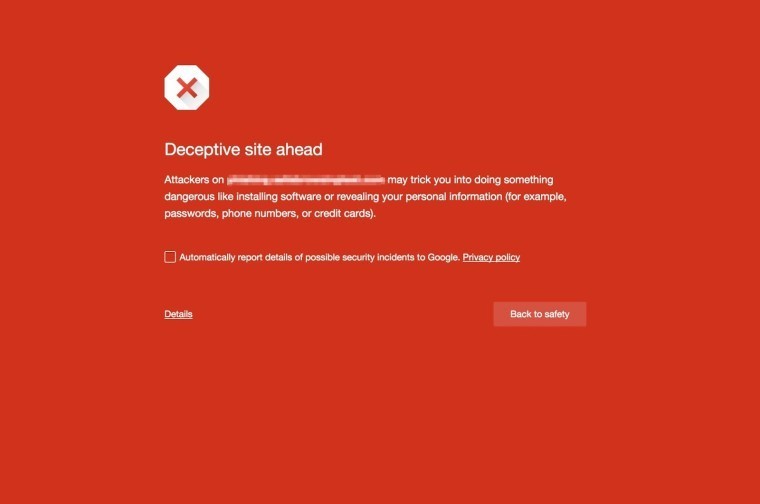
Google has recently announced its plans to start cracking down on websites that display deceptive ads. The company will begin warning users if they ever enter such places on the web with a message stating "deceptive site ahead", once they click on an ad it suspects contains "social engineered" content.
The company aims to lessen this significantly through its updated social engineering policy. It lists possible deceptive social engineered ads, some of which:
- Pretend to act, or look and feel, like a trusted entity — like your own device or browser, or the website itself.
- Try to trick you into doing something you’d only do for a trusted entity — like sharing a password or calling tech support.
These ads, like the images on the right, may come in a form of an alleged "download button," usually stating that a plugin needs to be installed in order for content on the website to be utilized. Another type of deceitful ad is one that states that a user's system is outdated, and that they should click on the illusory message box in order to keep their computer updated. And lastly, one of the most common tricks is an ad disguising as a download/play button for a streaming website.
Read more: Google to warn users about deceptive download buttons

A 26-year-old hacker has been sentenced to 334 years in prison for identity theft as well as mass bank fraud in Turkey, or in simple words, he has been sentenced to life in prison.
Named Onur Kopçak, the hacker was arrested in 2013 for operating a phishing website that impersonated bank site, tricking victims into providing their bank details including credit card information.
Read more: 26-Year-Old Hacker Sentenced to Record 334 Years in Prison
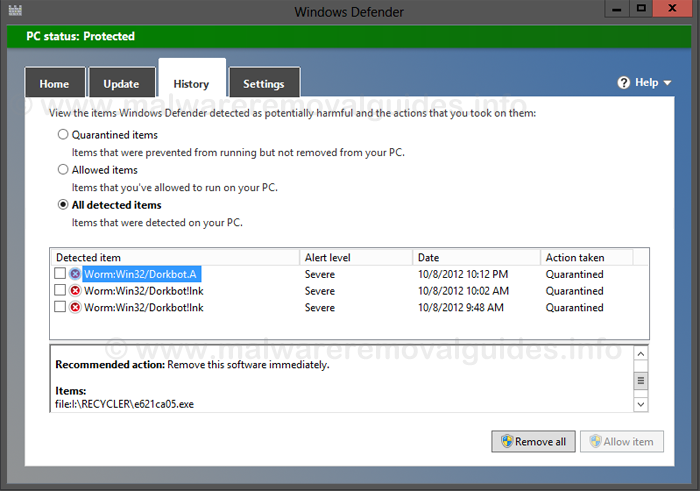
Discovered in 2011 the Win32/Dorkbot malware has spread to over a million Windows PCs worldwide. During the last six months alone it had been infecting over 100,000 machines a month. Microsoft announced on Wednesday they had teamed up to enact a coordinated malware eradication campaign to disrupt the botnet.
The malware has been spread via a number of routes including USB drives, IM clients, Social Networks, Email and Drive-by downloads. Its primary aim was to steal online user credentials and any information that can personally identify you. It is also able to install yet more malware to your PC from command and control servers.
Read more: Microsoft leads FBI & Interpol coalition to destroy million strong botnet
Read more: Dell installs self-signed root certificate on laptops, endangers users' privacy
TIPS & TRICKS ICT WORLD
- Codeigniter4: Howto fetch data by ID (button click) from database using JQuery Ajax
- Howto stop vulnerable Open Memcached on a Zimbra Server.
- Proxy Server not running on Zimbra Mail Server.
- Howto remove .php, .html extensions on a web page using .htaccess file
- How to Increase the Max Upload Size Limit
- Howto Create a Distribution List or Mailing List in Zimbra mail server
- Howto configure redirection/forward of specific user emails to another email address in Cpanel
- Restore WhatsApp Backup in Android and iPhone
- Howto backup your WhatsApp messages to your Google Drive.
- RESOLVED in JOOMLA3.9: “Error: Application Instantiation Error: Call to undefined method JApplicationHelper::getHash()”
- Howto configure Microsoft Outlook 2016
- How to embed a tweet in to any website (WordPress, Joomla and Drupal)
